Be vigilant and research before hitting the share button …
The Serious Danger Presented by ‘DeepFakes’ – Exclusive Expose’
Why you SHOULD be concerned about Deep Fakes
by Evelyn Macleod | Associate Writer | Eternal Affairs Media
Deepfakes in entertainment
Deepfakes are manipulated synthetic media, taking a video and changing the person in the video with someone else. What once was a painstaking task, using CGI to replace a person’s face in a video. Is now achieved with face recognition, deep learning machine and GAN technology, creating a deepfake only takes minutes and is available to anyone with access to a smartphone.
Deepfakes are entertaining, both in the theaters and at the comfort of your scrolling phone. They are perfect for the inquisitive and creative mind, bringing to life our questions of what if.
Example, ever wonder what it would be like for Will Smith to play the Neo character in The Matrix?
The Deepfake technology, facial recognition and deep learning, is also used in the filters that we use in social media, snapchat filters (puppy ears and tongue), bitmoji and Apple’s Animoji. You can have the technology to replace your likeness on to a celebrity, with apps like Reface.
Deepfakes are entertaining, but they are also insidious. This technology has its risks and it’s important to be aware of these dangers to protect yourself from deception.
We have moved past seeing is believing. Do not be deceived by your eyes. You can take the blue pill, STOP READING HERE, ignorance is bliss. Or you can take the red pill, wake up from the simulation, and continue reading.
A glitch in the matrix
Deepfakes gone wrong, being used for very real present evil:
- Perversion and Sexual exploitation/Revenge porn/blackmail
- Hacking
- Fake news-Social engineering (PsyOps)
Deepfake perversion
Women and children are the most vulnerable to sexual exploitation by deepfake technology. I would highly suggest not putting family pictures on social media. You never know who is lurking. Once a picture is on the web it leaves a digital footprint, and it can’t be erased.
Venmo, Facebook Join Tech Giants Demanding Clearview Stop Scraping (dailydot.com)
The technology has made it easy to take a picture, and placing it on a person performing sex acts. A scorned ex lover may then release it on public accounts, this is revenge porn. Character defamation and privacy laws broken should be reported to authorities.
People may be blackmailed, threaten to release a deepfake video to a spouse or place of employment. Receiving any threat of extortion by text, email or phone call, go to the authorities right away. File a police report. With the rise of deepfakes this has brought down the value of blackmail, because now anyone can claim a video is fake.
To protect your family, it is best not to post pictures of family, on social media, especially children. There is no way of stopping a person from saving a picture of your child and placing it on these videos. Pedophile, predators stalk hashtags, #bathtime #momlife.
Technology is a tool and not a toy, be cautious traveling the interwebs, a digital footprint and faceprint, be advised can and will be used against you. Teach family members how to safely use the web.
Best practices, live out private lives out of the public eye. Report any revenge porn and threats of blackmail to police. Report and flag also on social media. Although, please be advised social media protects predators more so than victims.
Twitter refused to take down a video of child pornography, the victim reported and flagged his own video. Sex traffickers targeted the child when he was 13. Released the videos of his abuse online, resurfaced on social media. Still report any graphic content on a social media site.
HACKING
Hackers use personal information collected to acquire passwords and access to bank accounts. Now with people living their lives on social media makes it easier to collect this information. We post everything, our place of employment, birthday, family relationships, spouse, siblings, parents, making it easy for hackers to collect our data.
Avoid the FaceBook quizzes, Nametest, you give them access to all your information on Facebook and sometimes in the fine print, access to your phone. Collecting and harvesting your information. Stop stepping up to every challenge trending with your facebook friends. The very question asked in those, get to know me posts are password challenge questions. Example: Elementary school? Best friend in school? Name of first pet? How many siblings?
Avoid answering every phone call, if you don’t recognize the number let it go to voicemail. Set voicemail greeting to a generic, AI greeting. Just as a video can be synthesized, so can a voice be synthesized, with only 5 seconds needed to get every articulation of vowel and consonant. With a voice deepfake doesn’t need to be a high quality, with a phone call, the excuse of poor reception.
Deepfake technology can clone your voice in seconds.
Answering a phone call: “Hello, who is this? Hello?? Wrong phone number, no, thank you”
To your synthetic voice calling your spouse, “I need our bank account information”
Creepy, and dangerous. Start to live your private life out of the public eye. Pictures that we have placed on our social media can be collected and harvested. That’s actually how facial recognition was perfected, using data sets scrapped from pictures on social media. Downloading a social media app gives them access to your microphone and camera.
Fake news-Social engineering (PsyOps)
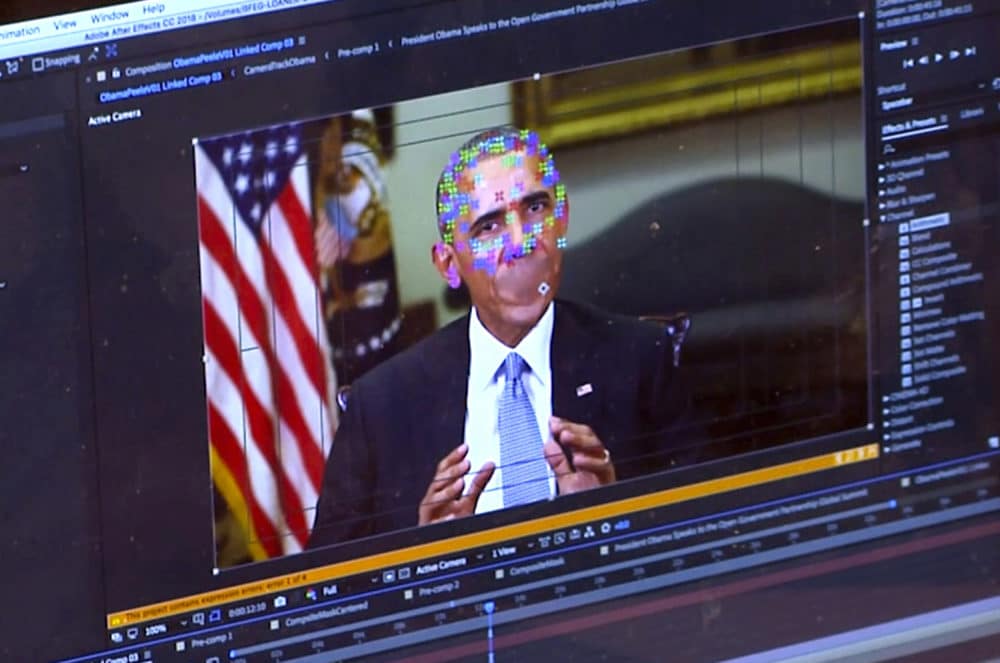
Social engineering is manipulating people into performing activities. This is a warning, all of your information is being harvested and collected. In the name of convenience we trade our privacy and security.
Online shopping, connecting with our friends online, smart watches tracking every step and heartbeat.
Every expression you leave on social media, like and dislike, is collected, Big Tech, Deep state, know your buttons and how to push them. Google has the power to surface up and suppress the information you see. Google also acquired Fitbit, smartwatches, the ability to track sleeping patterns and heart rates.
Google closes its Fitbit acquisition (cnbc.com)
Having that information to analyze demographic and reactions, is the first step in social engineering. Big Tech has access, to know what makes a person tick, knowledge of what information or misinformation needs to be released when a certain reaction is desired. Fear and anger is a great tool of the manipulator.
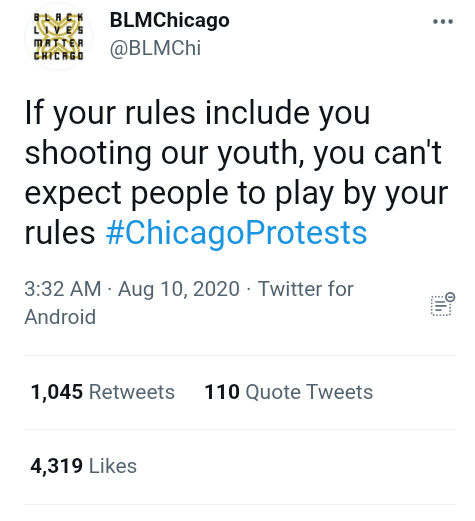
Case study Election year 2020: Area Chicago, Illinois August 2020
A chapter of Black Live Matter, in Chicago, released misinformation on twitter.
The boy was actually a 20 year old man, who was armed and firing at police.
The misinformation had gone viral and the reaction, wanted and desired was fulfilled, Chicago had a night of unrest, rioting and looting. The tweet with false information spread like wildfire and destroyed businesses and the reputation of Chicago PD.
Twitter does have the ability to throttle and suppress anything trending, to suspend any account with misinformation, to delete the tweet, but they allowed for this Tweet to spread.
Using deepfake technology one can create synthesized pictures to make it look like a real person. We have seen fake accounts created with these fake pictures. Sock puppet accounts are not a real person, but a real agenda is being pushed.
Deepfake used to attack activist couple shows new disinformation frontier | Reuters
Using deepfake technology and the fake news, Deep State can release a video, to get a response desired, aimed at a highly reactive demographic group. Perhaps next election cycle, it won’t be a fake tweet going viral but a Deepfake video. The ability to synthesize a brutal violent video to make it look like someone was murdered is here. Operation mockingbird repeats a story, names and location will change but the exact verbiage used. Be vigilant and research before hitting the share button.
To spot a deepfake will require the same technology to make one, artificial intelligence. They are getting more sophisticated and harder to spot if they are fake videos. Social Media Facebook and Twitter claim they have the ability to spot and identify. Considering what’s trending, identifying the deepfakes, will be used to censor those who oppose the Great Reset agenda. Put a real video out with a politician incriminating himself, but shortened the clip, Twitter can flag it as manipulated media.
With deepfake technology, the ability to not only synthesize the face, but also the body and voice. It is easy to create a synthesized media to bring a dead person to life. Hollywood has been using it for our entertainment, for the untimely deaths of actors, we can fool our mind, which is real which is fake. Actor Oliver Reed in The Gladiator, Actor Paul Walker in Fast and Furious franchise, Carrie Fisher in Star Wars franchise. If Hollywood has been doing it for years, don’t check it off that Deep State isn’t doing it as well.
Are you enjoying the simulation that a mentally incapacitated man can run this country? It’s not the first time. President Woodrow Wilson 1919 was very sick, his wife Edith hid the extent of his mini stroke from the press.
The dangers of deepfakes, spread of perversion, hacking, extortion, and manipulation. To spot a deepfake, the quality of the video will be poor, occlusions a blocked hand by a filter of the manipulated media, facial features not matching up with the emotions expressed in the voice.
Remember, faith is the substance of things hoped for, the evidence of things not seen.