New EvilProxy Phishing Service Allowing Cybercriminals to Bypass 2-Factor Security
Found On Dark Web: Beware Of Phishing – Hackers Are Finding New Ways To Bypass Two-Factor Authentication
Ravie Lakshmanan with The Hacker News reports:
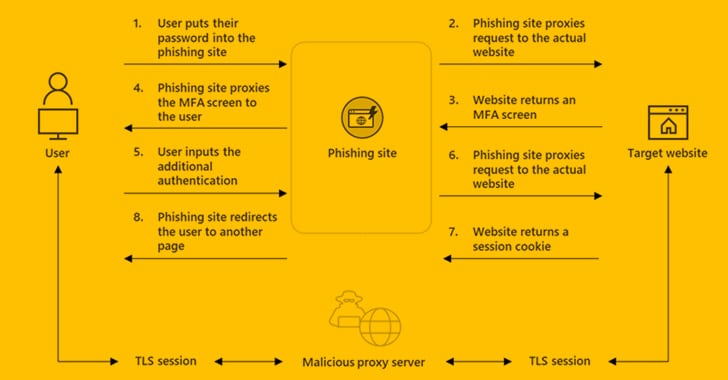
A new phishing-as-a-service (PhaaS) toolkit dubbed EvilProxy is being advertised on the criminal underground as a means for threat actors to bypass two-factor authentication (2FA) protections employed against online services.
“EvilProxy actors are using reverse proxy and cookie injection methods to bypass 2FA authentication – proxifying victim’s session,” Resecurity researchers said in a Monday write-up.
The platform generates phishing links that are nothing but cloned pages designed to compromise user accounts associated with Apple iCloud, Facebook, GoDaddy, GitHub, Google, Dropbox, Instagram, Microsoft, NPM, PyPI, RubyGems, Twitter, Yahoo, and Yandex, among others.